View Attack Analysis
This topic describes how to view attack Analysis on the Cloud.
Operation Steps
In the product management page, choose "Threat Detection Service".
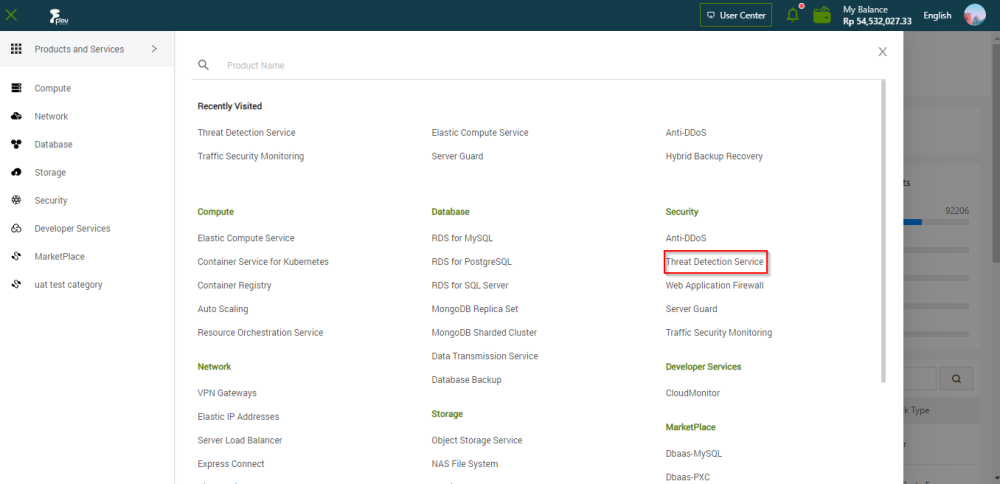
In the left-side navigation pane, click "Attack Analysis".
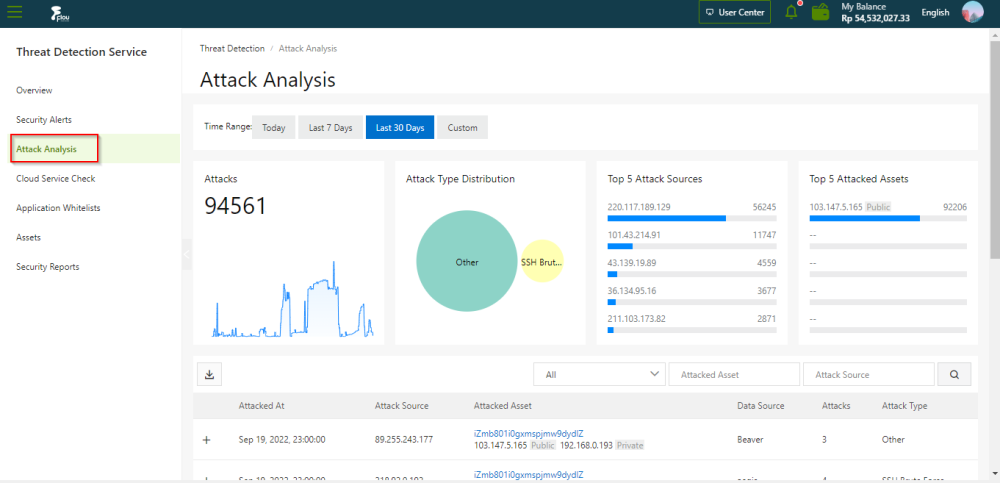
On the "Attack Analysis" tab , view the attack analysis information on the Cloud.
On the Attack Analysis page, you can specify a time range to view these attack details. You can view the attack analysis statistics of the current day, last 7 days, or last 15 days. You can also set Time Range to Custom to view the statistics of a time range within the last 30 days.
- Attacks: the total number of attacks detected in your assets within a specified time range.
- Attack Type Distribution: the attack types and the number of attacks for each type.
- Top 5 At t ack Sources: the top five IP addresses from which the most attacks are launched.
- Top 5 Attack Assets: the top five assets that are attacked the most frequently.
- Attack list: the details about each at tack . The details include the attack time, source IP address, attacked asset , attack type, and total number of attacks.
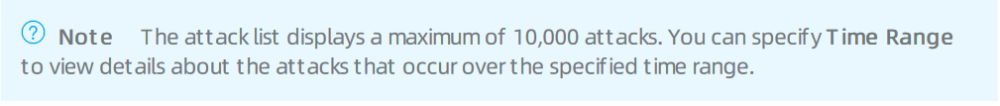
Parameters in the attack list.
- Search for an attack (Optional)
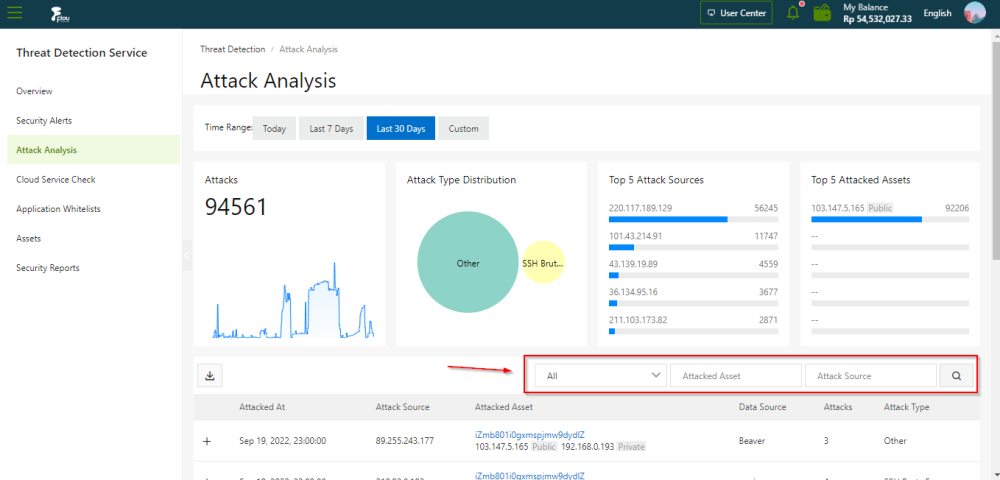
To search for an attack and view the details about the attack, specify search conditions above theattack list . Search conditions include the attack type, attacked asset, source IP address, and portnumber.
- View the details of anattacked asset (If any)
To view the details about an attacked asset , move the pointer over the name of the attacked asset.
- Export the attack list
To export and save the attack list to your computer, click the download icon in the upper- lieft corner above the attack list. The attack list is exported to an Excel file.