Add a TCP listener
Overview
This topic describes how to disable access control for a listener.
Procedure
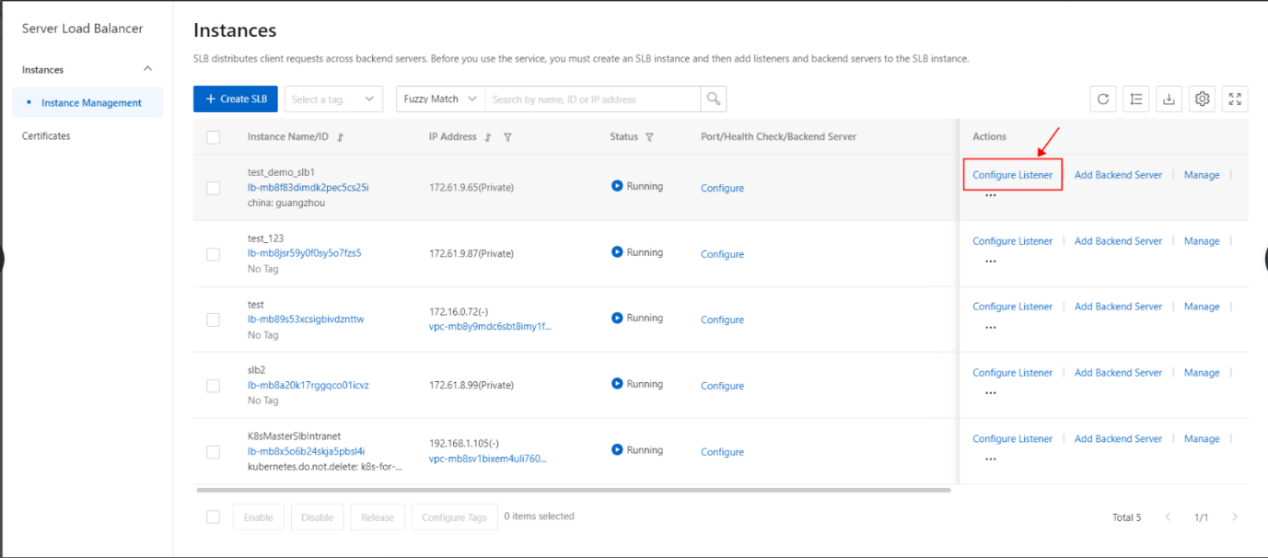
- On the SLB management console page, select the SLB instance to be operated and click Configure Listener or click to enter the SLB instance, on the monitoring page, click Add listener.
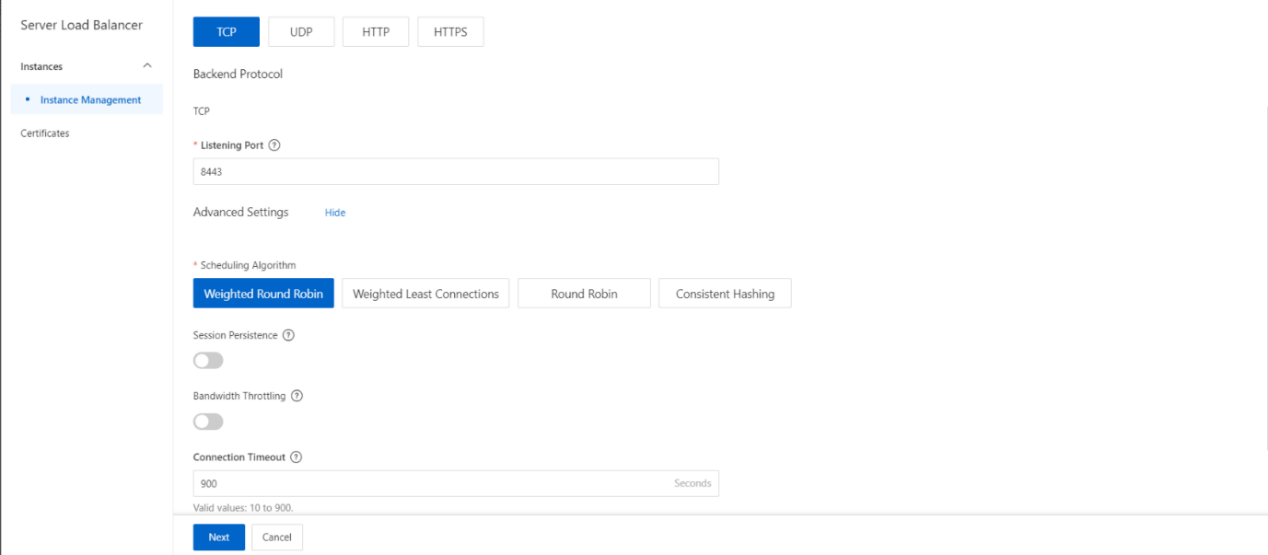
- Complete the following operations to configure the listening protocol, then click Next.
| Parameter | Description |
|---|---|
| Select Listener Protocol | Select TCP. |
| Listening Port | Specify the listening port that is used to receive and forward requests to backend servers. Valid values: 1 to 65535. |
| Listener Name | Enter a name for the listener. |
| Advanced | You can click Modify to configure the advanced settings. |
| Scheduling Algorithm | Select a scheduling algorithm. · Weighted Round-Robin ( WRR ) : Backend servers that have higher weights receive more requests than backend servers that have lower weights. · Round-Robin (RR) : Requests are distributed sequentially to backend servers. · Consistent Hash (CH) : · Tuple : specifies consistent hashing that is based on four factors: source IP address, destination IP address, source port, and destination port. Requests that contain the same information based on the four factors are distributed to the same backend server. · Source IP : specifies consistent hashing that is based on source IP addresses. Requests from the same source IP address are distributed to the same backend server. Note Only high-performance CLB instances support the CH algorithm. |
| Enable Session Persistence | Specify whether to enable session persistence. After session persistence is enabled, CLB forwards all requests from a client to the same backend server. For TCP listeners, session persistence is implemented based on IP addresses. Requests from the same IP address are forwarded to the same backend server. |
| Enable Access Control | Specify whether to enable access control. Select an access control method after you enable access control. Then, select an access control list (ACL) that is used as the whitelist or blacklist of the listener. · Whitelist: allows access from specific IP addresses. Only requests from the IP addresses or CIDR blocks specified in the network ACL are forwarded. Whitelists apply to scenarios in which you want to allow access only from specific IP addresses. Your service may be adversely affected if the whitelist is not properly configured. After a whitelist is configured, only requests from IP addresses that are added to the whitelist are forwarded by the listener. If a whitelist is configured but no IP address is added to the whitelist, the listener forwards all requests. ·Blacklist: denies access from specific IP addresses. Requests from the IP addresses or CIDR blocks specified in the network ACL are denied. Blacklists apply to scenarios in which you want to deny access from specific IP addresses. If a blacklist is configured but no IP address is added to the blacklist, the listener forwards all requests. Note IPv6 CLB instances can be associated only with IPv6 ACLs, while IPv4 CLB instances can be associated only with IPv4 ACLs. |
| Enable Peak Bandwidth Limit | Specify whether to set the maximum bandwidth of the listener. If the CLB instance is billed based on bandwidth usage, you can set different maximum bandwidth values for different listeners. This limits the amount of traffic that can be forwarded by each listener. The sum of the maximum bandwidth of all listeners that are added to a CLB instance cannot exceed the maximum bandwidth of the CLB instance. By default, this feature is disabled and all listeners share the bandwidth of the CLB instance. Note If a CLB instance is billed based on data transfer, the bandwidth of its listeners is not limited by default. |
| Connection Timeout | Specify the timeout period of idle TCP connections. Unit: seconds. Valid values: 10 to 900. |
| Proxy Protocol | Use the proxy protocol to pass client IP addresses to backend servers. Note You cannot enable this feature in scenarios where PrivateLink is used. |
| Obtain Client Source IP Address | Specify whether to retrieve the real IP addresses of clients. Only Layer 4 listeners support this feature. By default, this feature is enabled. |
| Automatically Enable Listener After Creation | Specify whether to immediately enable the listener after it is created. By default, listeners are enabled after they are created. |
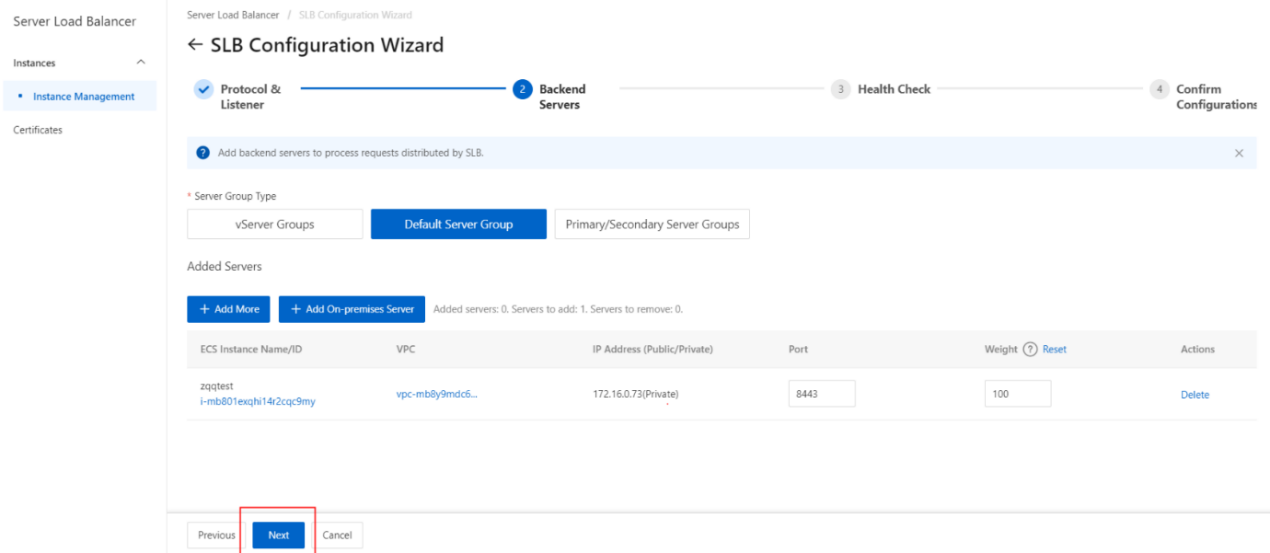
3. Add backend servers
After you configure the listener, you must add backend servers to process client requests. You can use the default server group that is configured for the SLB instance, or create a vServer group or a primary/secondary server group.
- On the Backend Servers wizard page, select Default Server Group and click Add More.
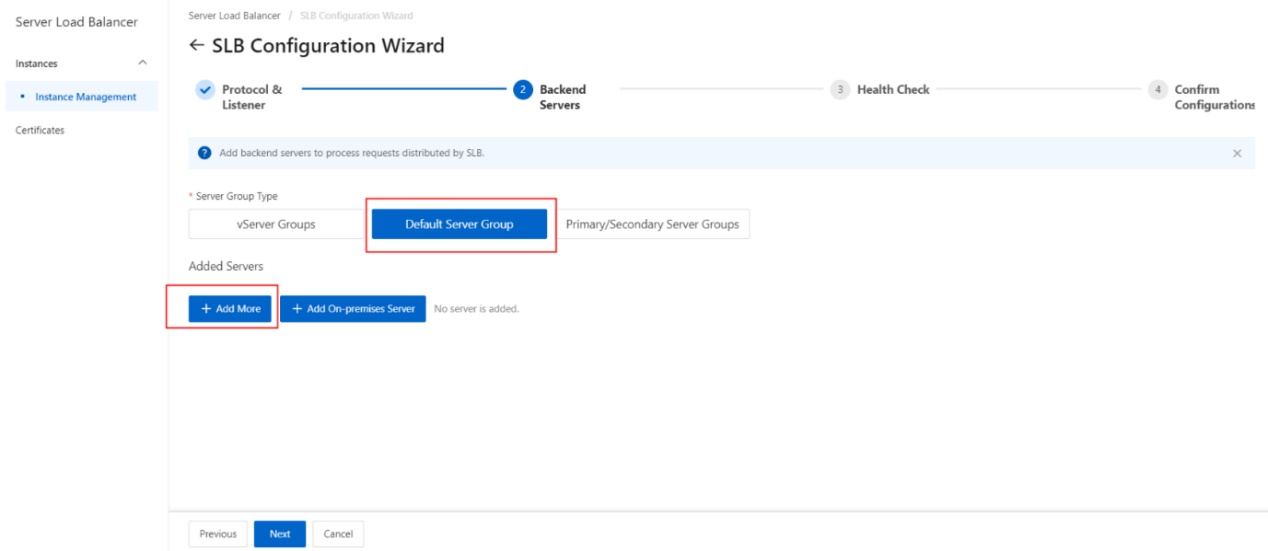
- In the My Servers panel, select the Elastic Compute Service (ECS) instances that you want to add as backend servers and click Next.
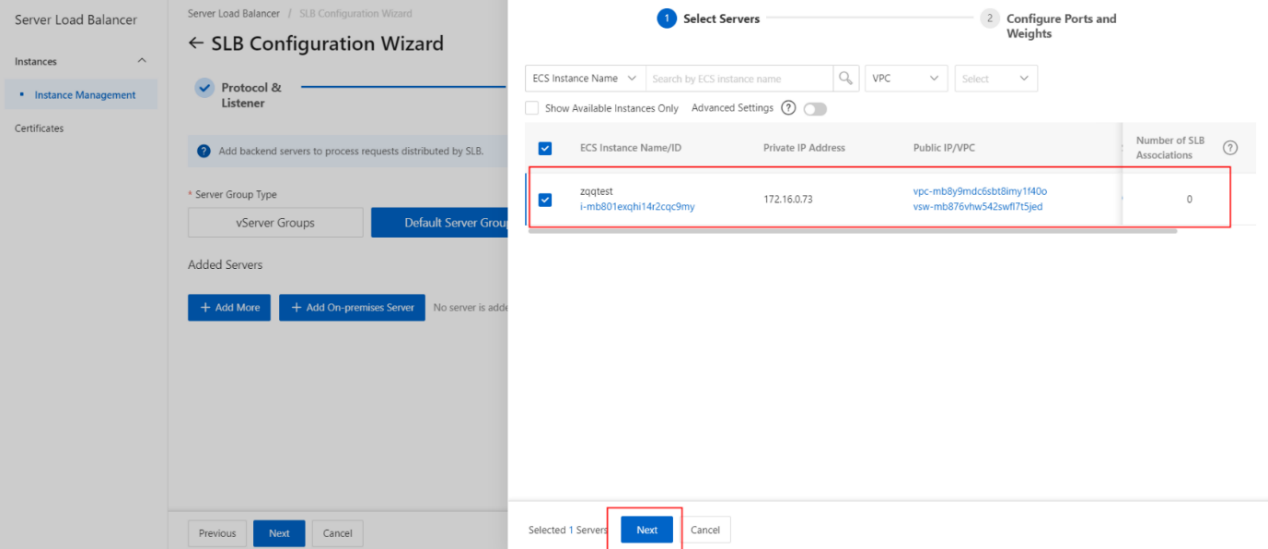
- On the Configure Port s and Weight s wizard page, specify the weights of the backend servers that you want to add. A backend server with a higher weight receives more requests.
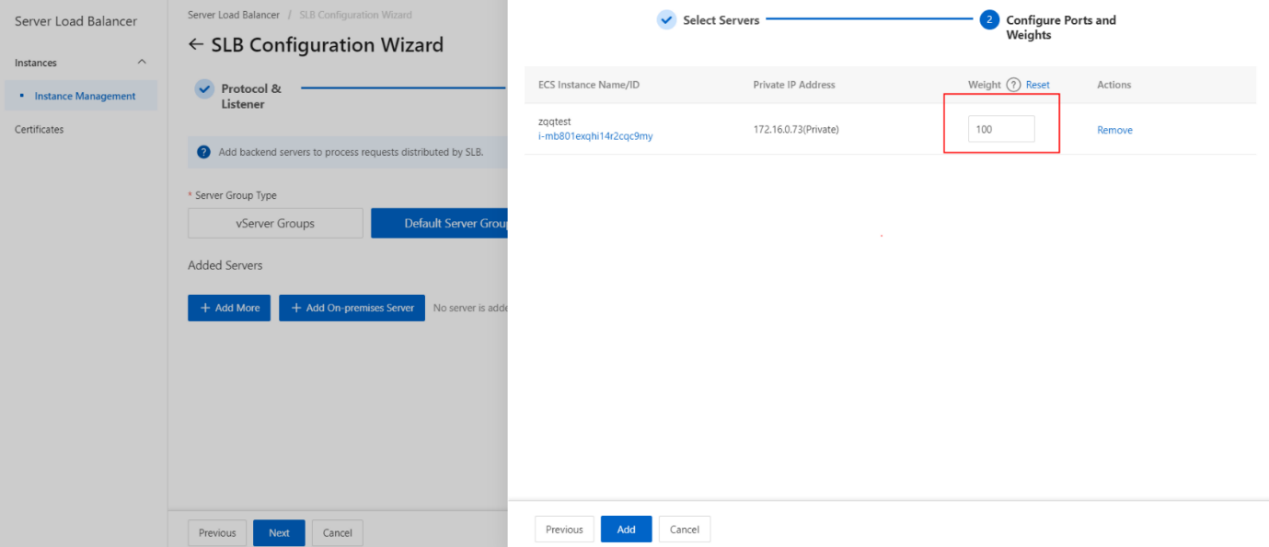
- Click Add. On the Default Server Group tab, specify the ports that you want to open on the backend servers to receive requests. The backend servers are the ECS instances that you selected. Valid values: 1 to 65535.
You can specify the same port on different backend servers that are added to an SLB instance.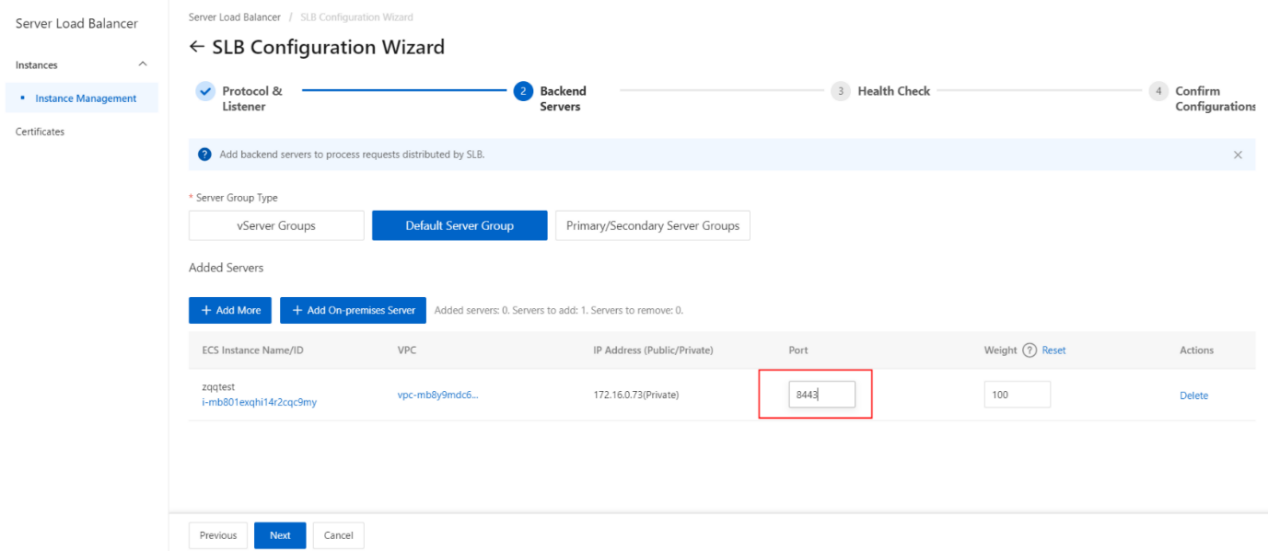
- Click Next.
- Configure health checks.
CLB performs health checks to check the availability of the ECS instances that serve as backend servers. The health check feature improves overall service availability and reduces the impact of backend server failures.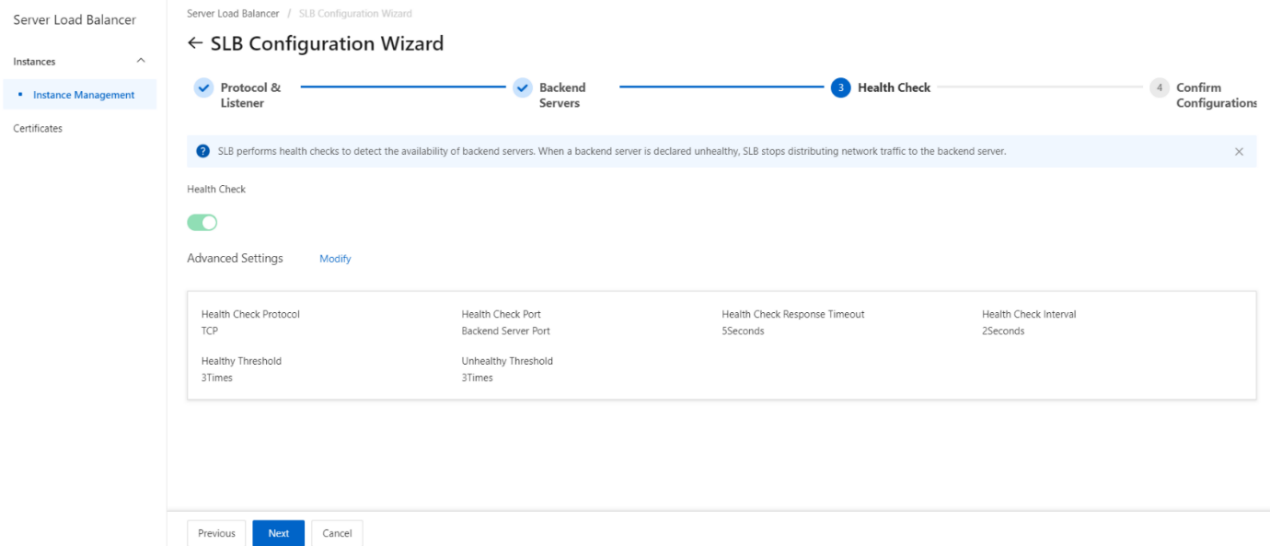
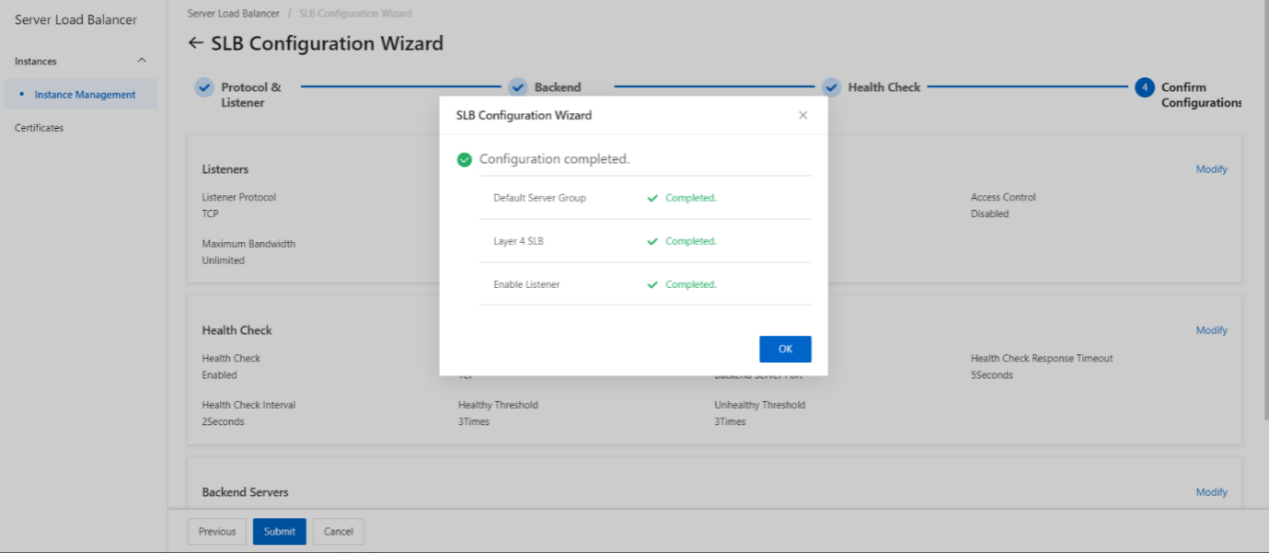
- Submit the configurations.
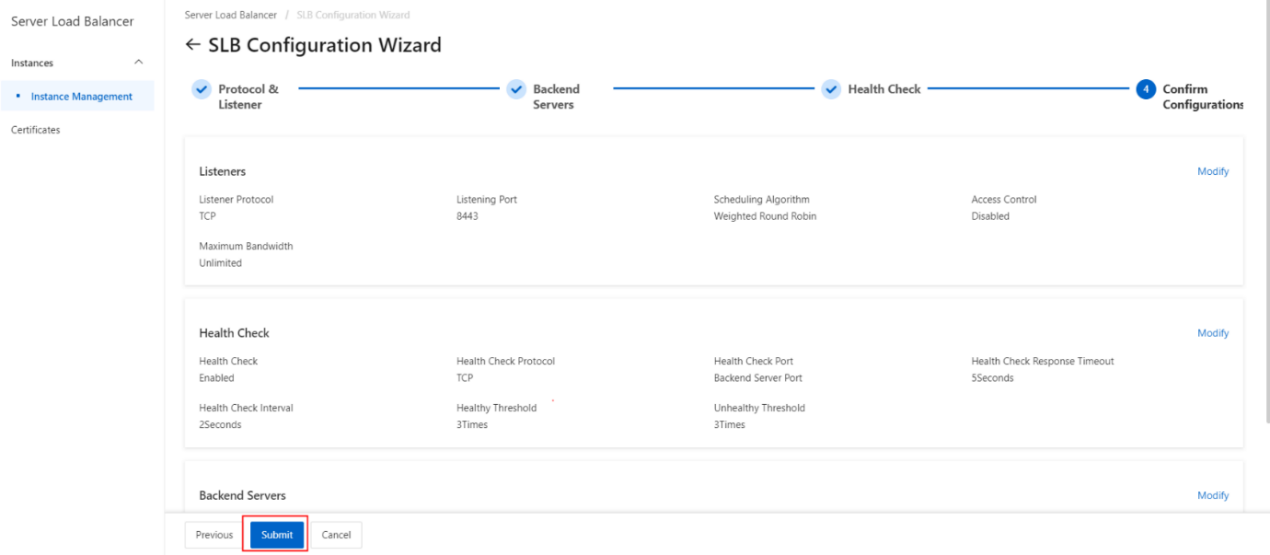
- TCP listener configuration complete.