Add a HTTPS listener
Overview
This topic describes how to add an HTTPS listener to a Server Load Balancer( SLB) instance. HTTPS is intended for applications that require encrypted data transmission. You can add an HTTPS listener to forward HTTPS requests.
Procedure
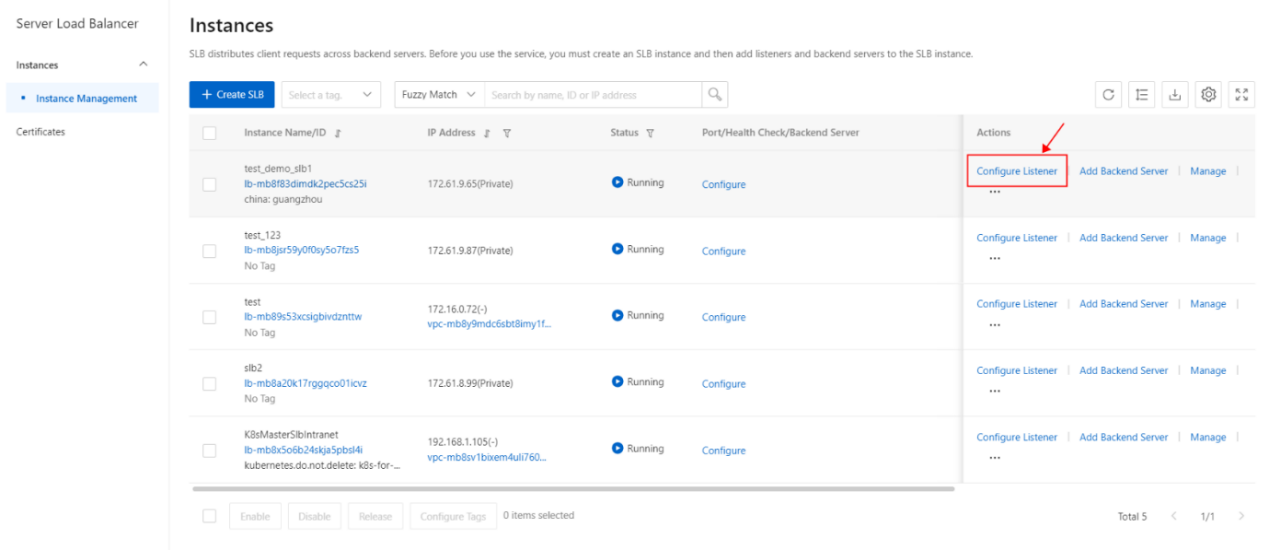
- On the SLB management console page, select the SLB instance to be operated and click Configure Listener or click to enter the SLB instance, on the monitoring page, click Add listener.
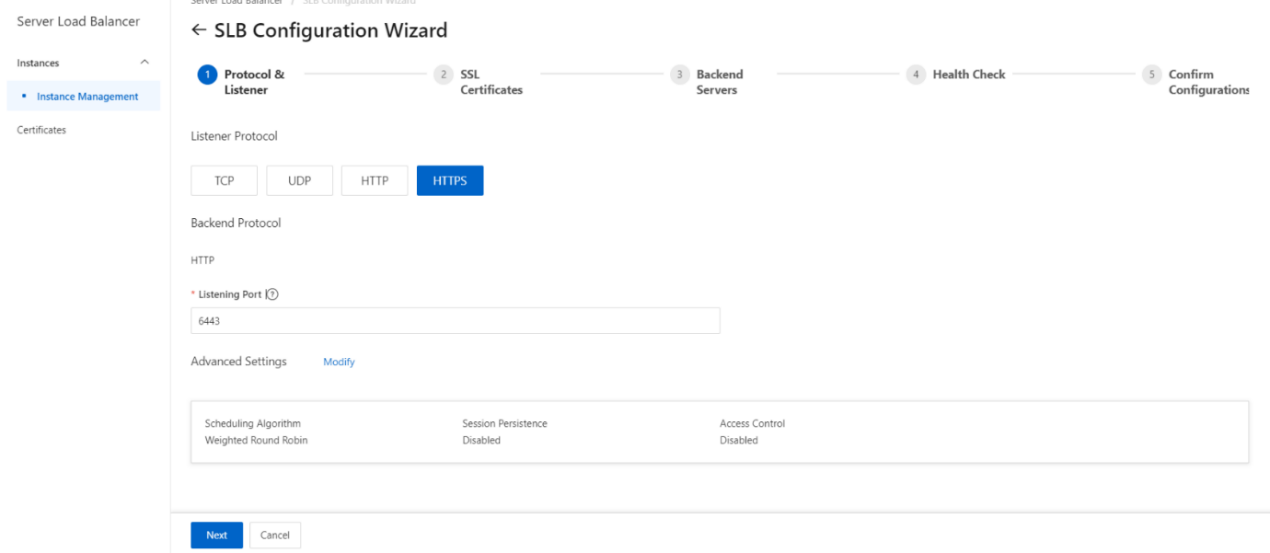
- Complete the following operations to configure the listening protocol, then click Next.
| Parameter | Description |
|---|---|
| Select Listener Protocol | Select the protocol of the listener. HTTPS is selected in this example. |
| Backend Protocol | In this example, HTTPS listener is required. Therefore, Backend Protocol is set to HTTP . |
| Listening Port | Specify a listening port to receive requests and forward them to backend servers. Valid values: 1 to 65535. |
| Listener Name | Specify a name for the listener. |
| Scheduling Algorithm | Select a scheduling algorithm. · Weighted Round-Robin ( WRR ) : Backend servers that have higher weights receive more requests than backend servers that have lower weights. · Round-Robin (RR) : Requests are distributed to backend servers in sequence. |
| Enable Session Persistence | Specify whether to enable session persistence. After session persistence is enabled, CLB forwards all requests from a client to the same backend server. Cookie Persistence · Insert cookie : If you select this option, you need to only specify the timeout period of the cookie. CLB inserts a cookie ( SERVERID ) into the first HTTP or HTTPS response that is sent to a client. The next request from the client carries this cookie, and the listener will forward this request to the recorded backend server. Persistent Timeout : If you select Insert cookie , you must specify the timeout period for session persistence. Valid values: 1 to 86400. Unit: seconds. · Rewrite cookie : If you select this option, you can specify the cookie that you want to insert into an HTTP or HTTPS response. You must specify the timeout period and the lifetime of a cookie on a backend server. After you specify a cookie, CLB overwrites the original cookie with the specified cookie. The next time CLB receives a client request that carries the specified cookie, the listener distributes the request to the recorded backend server. Cookie Name : If you select Rewrite cookie, you must specify a name for the cookie. The name can contain letters, digits, underscores (_), and hyphens (-). |
| Enable HTTP/2 | Select whether to enable HTTP/2 support for the CLB instance. |
| Enable Access Control | Specify whether to enable access control. Select an access control method after you enable access control. Then, select a network access control list (ACL) as the whitelist or blacklist of the listener. · Whitelist: allows access from specific IP addresses. Only requests from the IP addresses or CIDR blocks specified in the network ACL are forwarded. Whitelists apply to scenarios in which you want to allow access only from specific IP addresses. Your service may be adversely affected if the whitelist is not properly configured. After a whitelist is configured, only requests from IP addresses that are added to the whitelist are forwarded by the listener. If a whitelist is configured but no IP address is added to the whitelist, the listener forwards all requests. · Blacklist: denies access from specific IP addresses. Requests from the IP addresses or CIDR blocks specified in the network ACL are denied. Blacklists apply to scenarios in which you want to deny access from specific IP addresses. If a blacklist is configured but no IP address is added to the blacklist, the listener forwards all requests. Note IPv6 instances can be associated only with IPv6 network ACLs, and IPv4 instances can be associated only with IPv4 network ACLs. |
| Enable Peak Bandwidth Limit | Specify whether to set the bandwidth limit of the listener. If the CLB instance is billed based on bandwidth usage, you can set different maximum bandwidth values for different listeners. This limits the amount of traffic that can be forwarded by each listener. The sum of the maximum bandwidth of all listeners that are added to a CLB instance cannot exceed the maximum bandwidth of the CLB instance. By default, this feature is disabled and all listeners share the bandwidth of the CLB instance. Note If a pay-by-data-transfer CLB instance is used, the bandwidth of its listeners is not limited by default. |
| Idle Timeout | Specify a timeout period for idle connections. Unit: seconds. Valid values: 1 to 60. If no request is received within the specified timeout period, CLB closes the connection. When another request is received, CLB establishes a new connection. |
| Connection Request Timeout | Specify a request timeout period. Unit: seconds. Valid values: 1 to 180. If no response is received from a backend server within the specified timeout period, CLB returns the HTTP 504 status code to the client. |
| Gzip Compression | If you enable Gzip compression, files of specific types are compressed. If you disable Gzip compression, no file is compressed. Gzip supports the following file types: text/xml, text/plain, text/css, application/javascript, application/x-javascript, application/rss+xml, application/atom+xml, and application/xml. |
| Add HTTP Header Fields | Supported headers: · X-Forwarded-For: Add the header to retrieve client IP addresses. · SLB-ID: Add the header to retrieve the ID of the CLB instance. · SLB-IP: Add the header to retrieve the IP address of the CLB instance. · X-Forwarded-Proto: Add the header to retrieve the listening protocol. · X-Forwarded-Port: Add the header to retrieve the listening port. · X-Forwarded-Client- srcport : Add the header to retrieve client ports. |
| Client IP Address Preservation | Specify whether to retrieve client IP addresses. By default, this feature is enabled. |
| Automatically Enable Listener | Specify whether to immediately enable the listener after it is created. By default, listeners are enabled after they are created. |
| WAF Protection | SSpecify whether to enable Web Application Firewall (WAF) protection for the listener. |
3. Configure an SSL certificate.
To add an HTTPS listener, you must upload a server certificate or CA certificate. The following table describes the two types of certificates.
| Certificate | Description | Required for one-way authentication | DescriRequired for mutual authenticationption |
|---|---|---|---|
| Server certificate | A server certificate is used to authenticate the identity of a server. A browser authenticates the identity of a server by checking whether the certificate sent by the server is issued by a trusted CA. | Yes You must upload the server certificate to the certificate management system of CLB. | Yes You must upload the server certificate to the certificate management system of CLB. |
| Client certificate | A client certificate is used to authenticate the identity of a client. A server authenticates the identity of a client by verifying the certificate sent by the client. You can sign a client certificate with a self-signed CA certificate. | No | Yes You must install the client certificate on the client. |
| CA certificate | A CA certificate is used by a server to verify the signature of a client certificate. If the signature is invalid, the connection request is denied. | No | Yes You must upload the CA certificate to the certificate management system of CLB . |
| TLS security policy | TLS security policies are supported only by high-performance CLB instances. A TLS security policy contains TLS protocol versions and cipher suites that are available for HTTPS. | Yes | Yes |
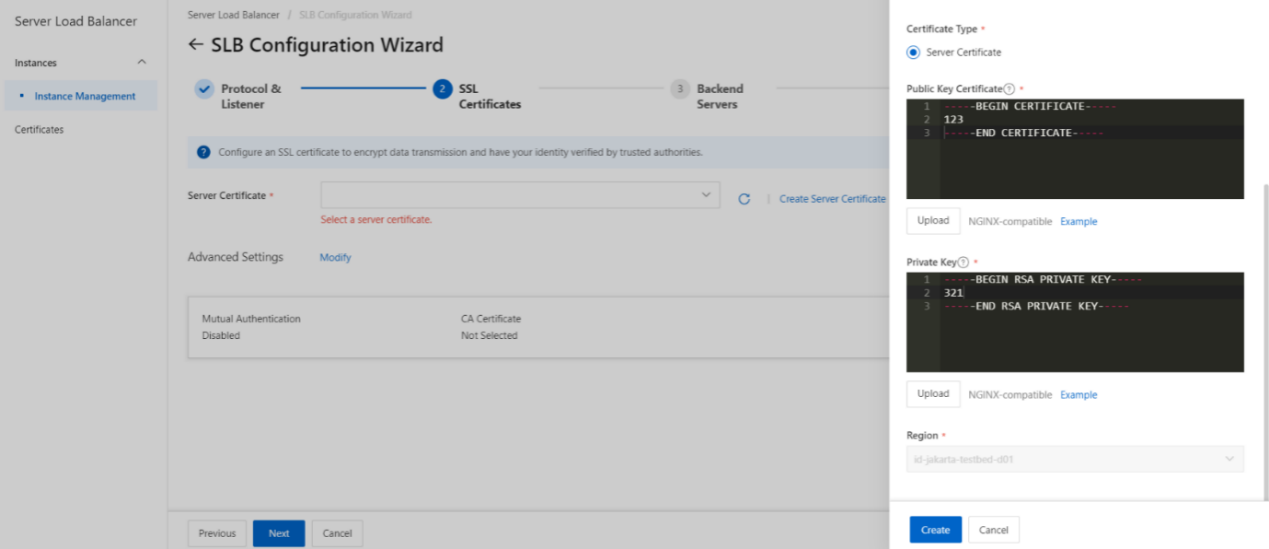
Before you upload a certificate, take note of the following rules:
- CLB supports the following public key algorithms: RSA 1024, RSA 2048, RSA 4096, ECDSA P-256, ECDSA P-384, and ECDSA P-521.
- The certificate that you want to upload must be in the PEM format.
- After you upload a certificate to CLB , CLB can manage the certificate. You do not need to associate the certificate with backend servers.
- It may take a few minutes to upload, load, and verify the certificate. Therefore, an HTTPS listener is not available immediately after it is created. It requires about 1 to 3 minutes to enable an HTTPS listener.
- The ECDHE cipher suite used by HTTPS listeners supports forward secrecy. It does not support the security enhancement parameters that are required by the DHE cipher suite. Therefore, you cannot upload certificates (PEM files) that contain the BEGIN DH PARAMETERS field.
- By default, the timeout period of session tickets for HTTPS listeners is 300 seconds.
- The actual amount of data transfer on an HTTPS listener is larger than the billed amount because a portion of data is used for handshaking.
- Therefore, the amount of data transfer greatly increases when a large number of connections are established.
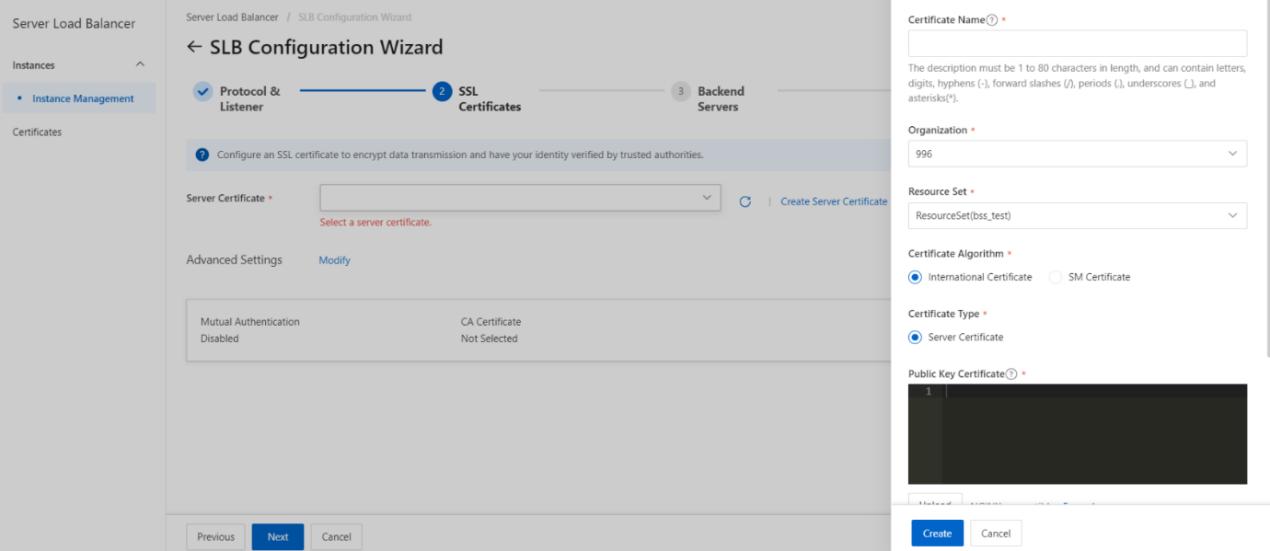
On the SSL Certificates wizard page, select the server certificate that you uploaded. You can also click Create Server Certificate to upload a server certificate.
To enable mutual authentication or configure a TLS security policy, click Modify next to Advanced.
Enable mutual authentication, and select an uploaded CA certificate. You can also upload a CA certificate.
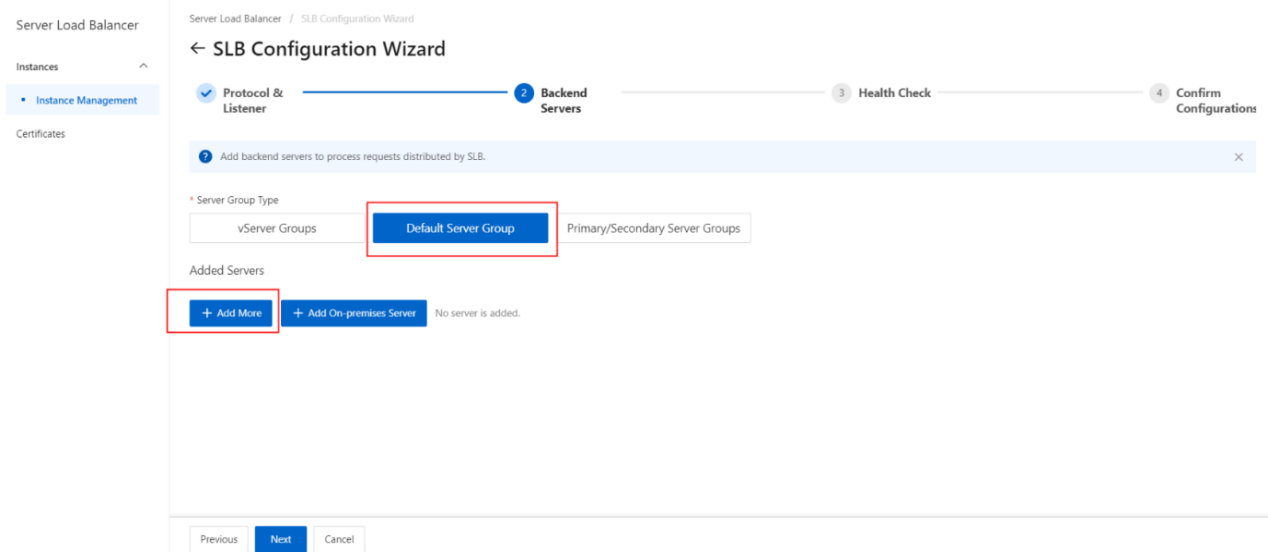
- Add backend servers.
After you configure the listener, you must add backend servers to process client requests. You can use the default server group that is configured for the SLB instance, or create a vServer group or a primary/secondary server group.
- On the Backend Servers wizard page, select Default Server Group and click Add More.
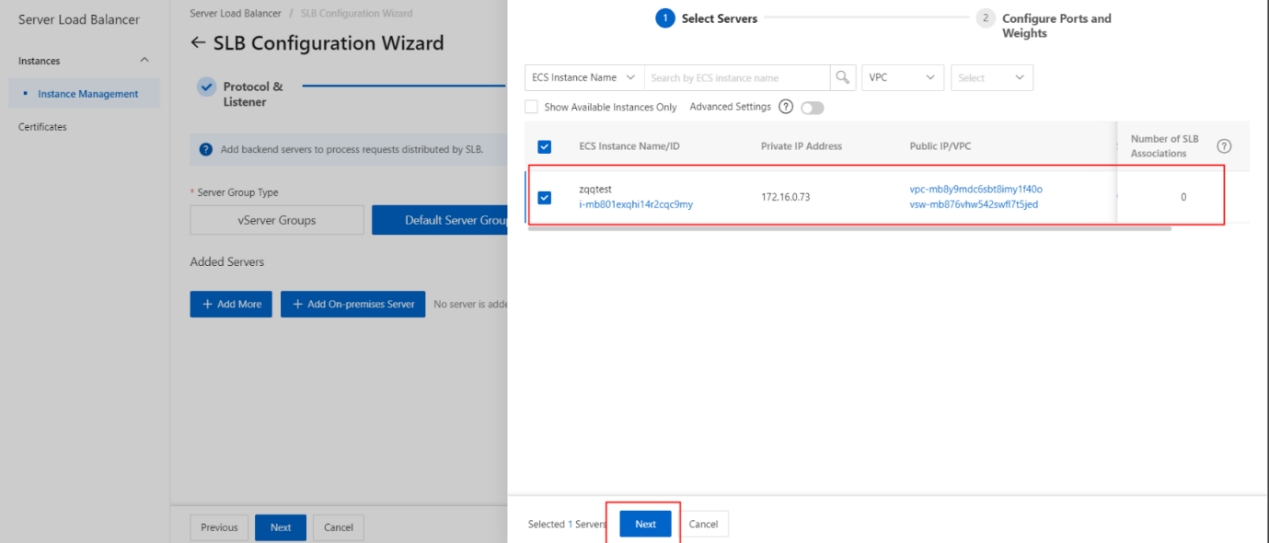
- In the My Servers panel, select the Elastic Compute Service (ECS) instances that you want to add as backend servers and click Next.
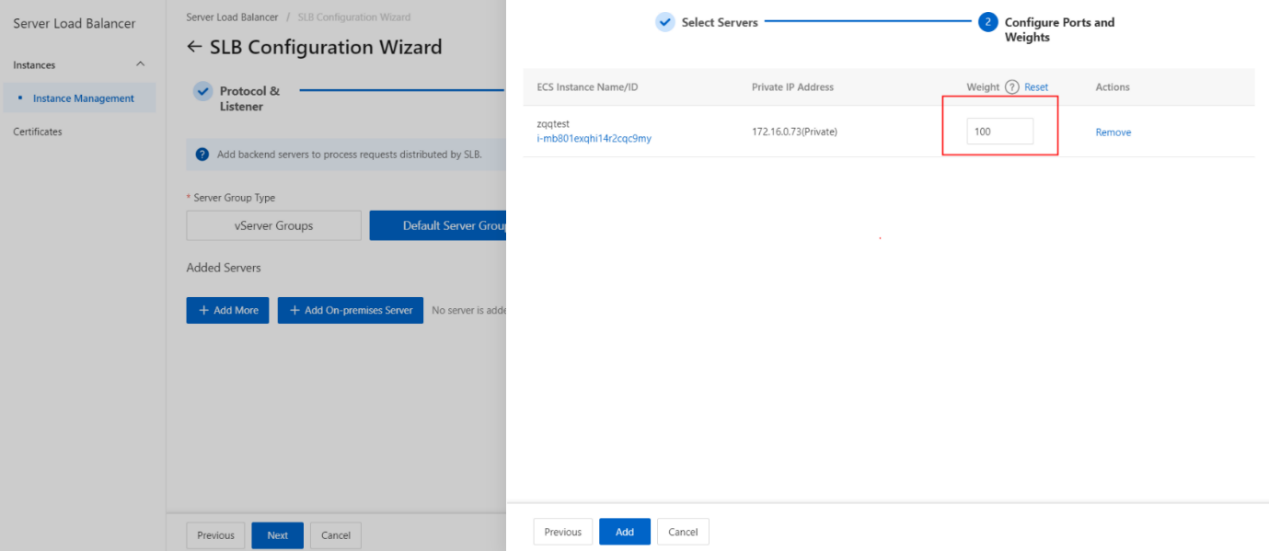
- On the Configure Port s and Weight s wizard page, specify the weights of the backend servers that you want to add. A backend server with a higher weight receives more requests.
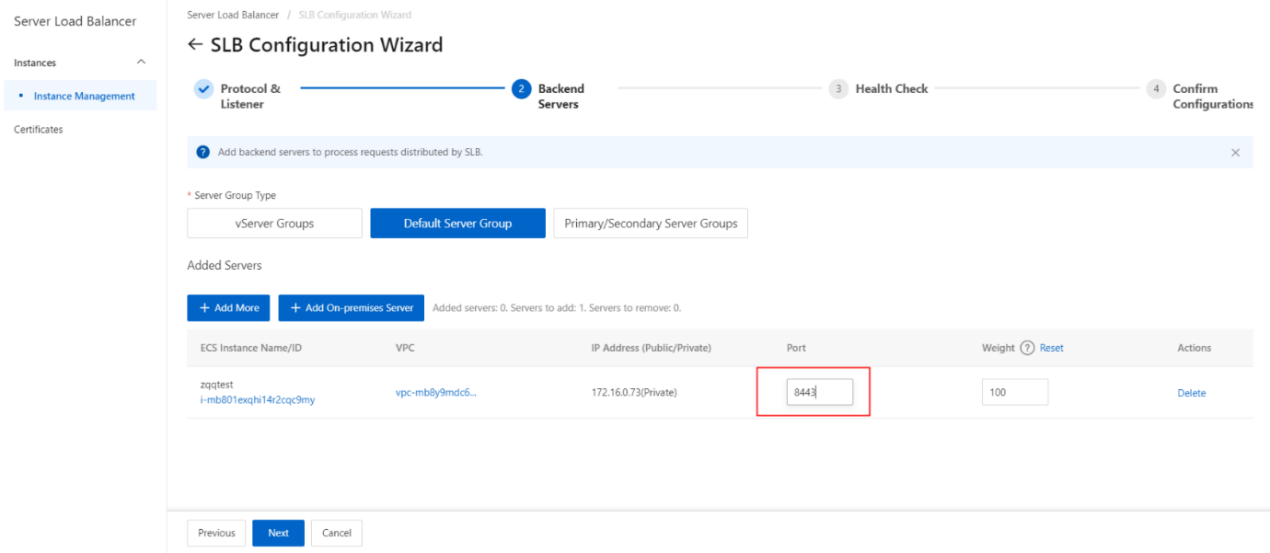
- Click Add. On the Default Server Group tab, specify the ports that you want to open on the backend servers to receive requests. The backend servers are the ECS instances that you selected. Valid values: 1 to 65535.You can specify the same port on different backend servers that are added to an SLB instance.
- Click Next.
- Configure health checks.
CLB performs health checks to check the availability of the ECS instances that serve as backend servers. The health check feature improves overall service availability and reduces the impact of backend server failures.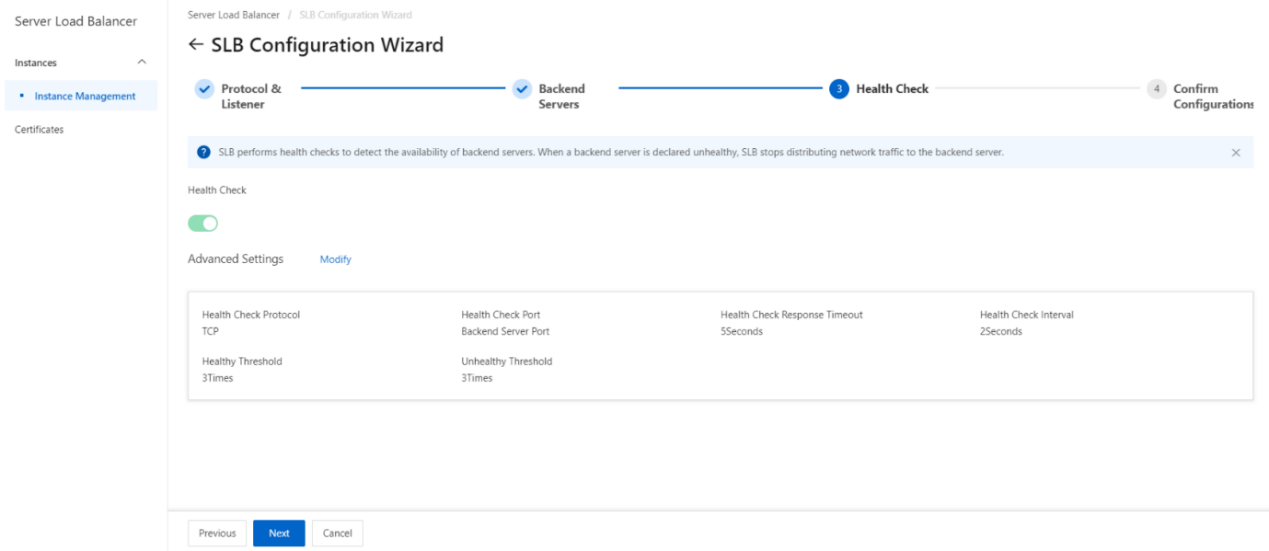
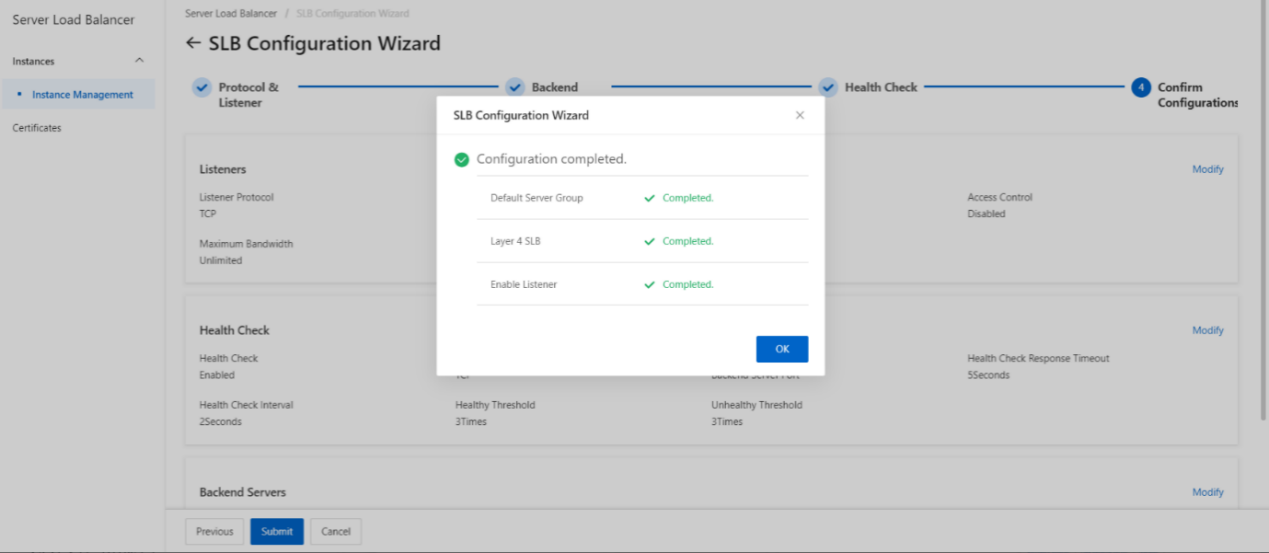
- Submit the configurations.
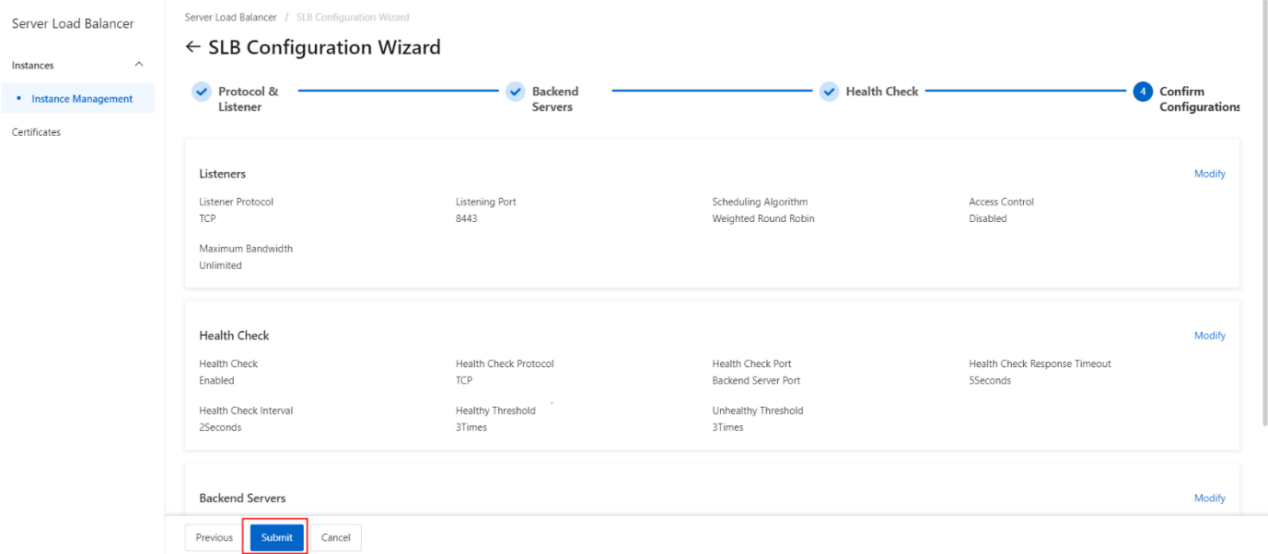
- Https listener configuration complete.