Configure vulnerability management policies
You can enable or disable automatic detection for different types of vulnerabilities and enable vulnerability detection for specific servers. You can also set a time duration for which invalid vulnerabilities are retained and configure a vulnerability whitelist.
Context
A vulnerability whitelist allows you to exclude vulnerabilities from the detection list. You can add multiplevulnerabilities in the vulnerability list to the whitelist. The system does not detect vulnerabilities that are added to the whitelist. You can manage the vulnerability whitelist on the vulnerability settings page.
Operation Steps
In the product management page, choose "Server Guard".
In the left-side navigation pane, click "Threat Prevention"> "Vulnerabilities".
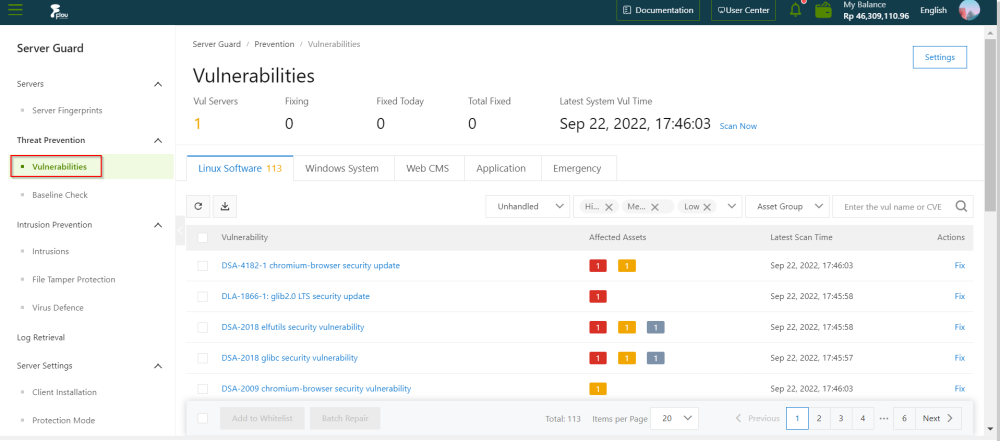
In the upper-right corner, click Settings to configure vulnerability management policies.
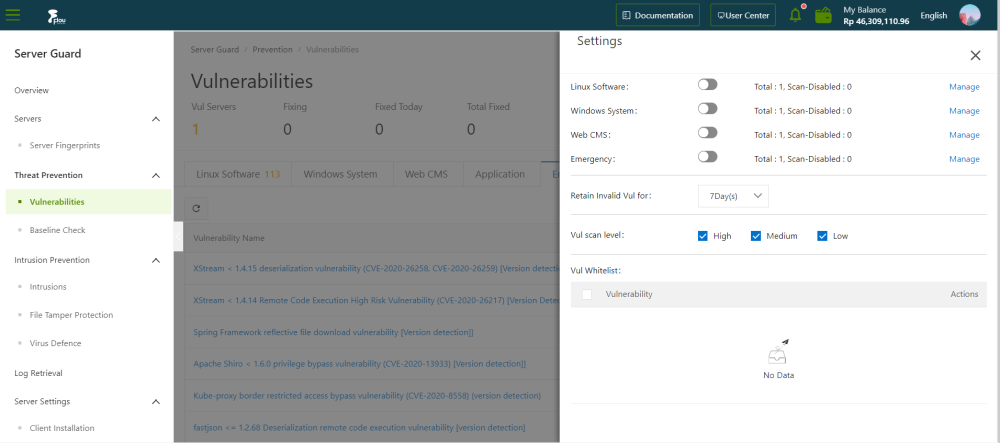
- Select a vulnerability type and enable or disable detection for vulnerabilities of this type.
- Click Manage next to a vulnerability type and specify the servers on which vulnerabilities of this type are detected.
- Select a time duration during which invalid vulnerabilities are retained. For example, you can select 7 days, 30 days, or 90 days
If you do not take an action on a detected vulnerability, the system determines that the alert is invalid. The system deletes the vulnerability after the specified duration.
- Select the vulnerability severities for scanning.
- High: Vulnerabilities of this severity must be fixed as soon as possible.
- Medium: Vulnerabilities of this severity can be fixed later.
- Low: Vulnerabilities of this severity are less urgent and can be fixed later.
- Select in the whitelist and click Remove to enable the system to detect these vulnerabilities and generate alerts for these vulnerabilities.